This blog post aims to unfold the details of DPI, exploring its definition, methods, applications, modern technologies, and the challenges it presents in the ever-evolving landscape of cybersecurity.
Introduction to DPI
When it comes to the DPI, it is a more sophisticated technology than normal packet inspection. It plays a crucial role in understanding, analyzing, and managing the complex flow of data across networks. In the vast landscape of network security and traffic management, one term that frequently surfaces are DPI.

In this blog post, we will dive into the depths of Deep Packet Inspection, exploring its definitions, methods, and diverse applications.
Understanding Deep Packet Inspection
Packet inspection can be categorized into two parts as:
Shallow Packet Inspection
Analyze upto layer 4 of OSI Layer model.
Deep packet Inspection
Analyze up to layer 7 in OSI model (Visibility of all the layers).
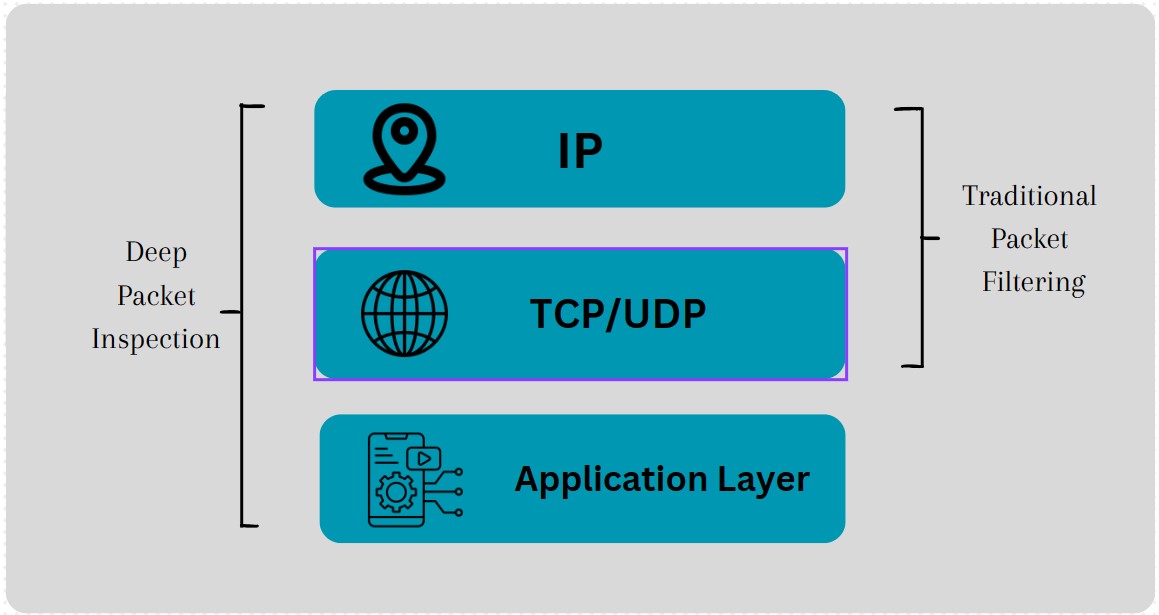
This granular level of examination provides a wealth of information about the nature and purpose of the data.
Conventional Packet Filtering vs. Deep Packet Inspection
Conventional Packet Filtering
Conventional packet filtering (Shallow Packet Inspection) primarily examines the header information of data packets, making decisions based on source and destination addresses, ports, and protocols.
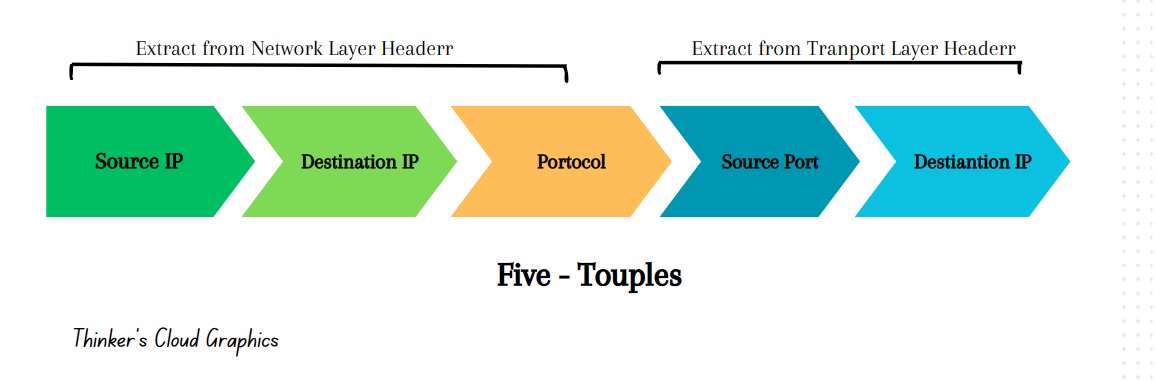
Using the above 5 details, we can categorize all the packets traversing through a network into sessions. A session is a packet exchange between two entities having above five-tuple fixed during the session.
- Five Tuple
- Source IP address
- Destination IP address
- Source Port
- Destination Port
- IP protocol
It operates at the network layer of the OSI (Open Systems Interconnection) model and is effective for basic traffic categorization as sessions for the purposes of basic traffic analytics and control but lacks the depth required for detailed analysis.
Deep Packet Inspection
Methods of Deep Packet Inspection
1. Signature-Based Inspection
This is one of the basic methods identifies that known patterns or signatures within packet payloads, enabling the detection of specific applications, protocols, or threats.
Here, the content of the packets is compared against a database of predefined signatures. These signatures represent patterns associated with known applications, threats, viruses, malware, or other undesirable content.
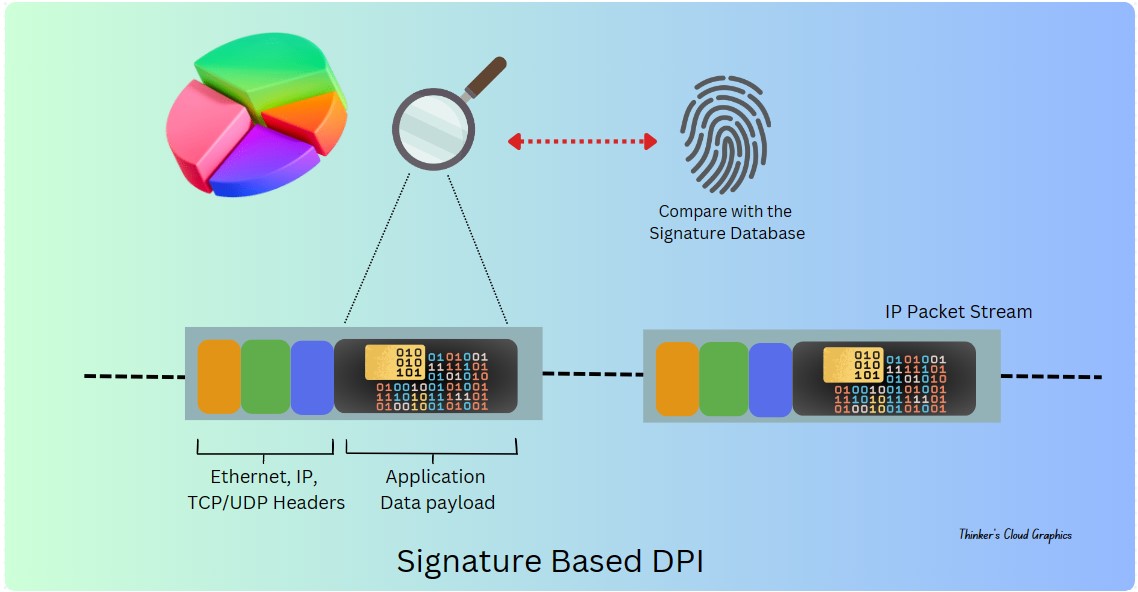
Basically, this acts as mapping a set of bytes against a known byte pattern. Those signatures need to be updated regularly according to new applications or new threats by network engineers.
2. String Matching Analysis
Many applications have textual identifiers that are contained within the payload part of the IP packets. We can use those specific words or phrases to identify the applications and even extract more sophisticated details of the users as well. (http request packets: user agent string contains Device info; Model, OS, Browser,..etc.)
3. Heuristic-Based Inspection
Uses algorithms and rules to identify deviations from normal patterns, allowing the detection of previously unknown threats or anomalies. Here we are defining a set of rules which can be used to clearly identify normal vs. abnormal behavior of sessions.
4. Behavioral Analysis
Monitors and analyzes the behavior of network traffic over time, establishing baselines for normal behavior and detecting unusual patterns.
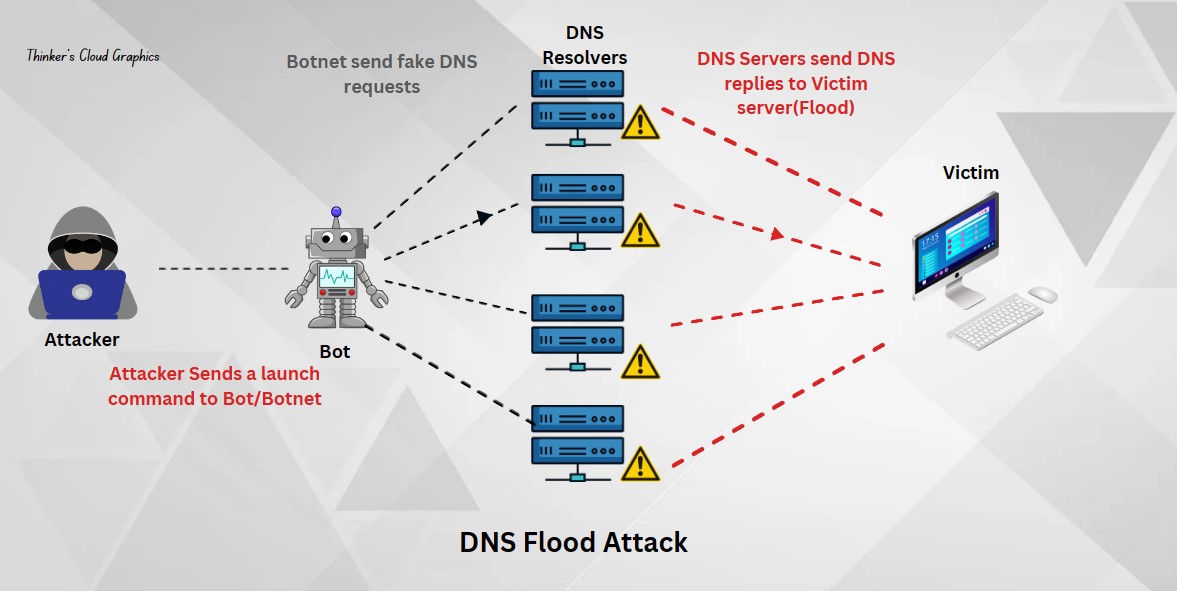
This is helpful to identify possible threats within a network such as cyber attacks. Ex: Whenever a DoS(Denial of Service) or DDoS(Distributed Denial of Service) attack happens, it can cause an unusual behaviour such as abnormally high amount of DNS requests (DNS floods), so suspicios traffic originating from a single IP or a subnet and sudden increment in bandwidths.
5. Numerical Property Analysis
There are many other properties that we can track with the time related to the statistics of network sessions such as
- packet/payload sizes
- Packet Timing
- Throughput
- Connection Duration
By monitoring the trends of those properties over time, we can come up with analytic conclusions about the sessions. This can help in identifying patterns or anomalies associated with certain types of traffic.
A Challenge for DPI “Data Encryption”
As encryption becomes more widespread, DPI faces challenges in inspecting encrypted traffic, leading to blind spots in threat detection. There are multiple encryption protocols and algorithms in use, such as TLS (Transport Layer Security) for web traffic and end-to-end encryption in messaging applications. Those are really challenging situations for DPI since the deeper details cannot be extracted using the encrypted payload with many of the existing DPI techniques.
Modern Technologies of DPI
Machine Learning and AI for DPI
DPI leverages machine learning algorithms and artificial intelligence to enhance its ability to identify and respond to evolving threats.
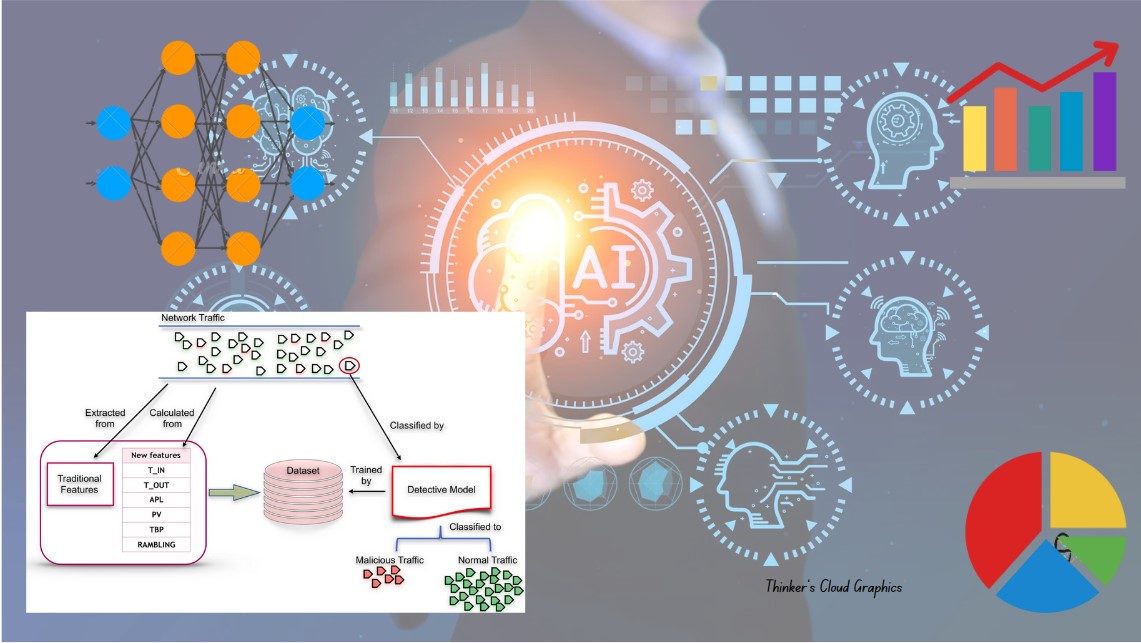
Machine learning algorithms enable the classification of network traffic by training models on known categories. These models can automatically identify and classify new traffic. Common algorithms used for this purpose include decision trees, support vector machines (SVM), and Naive Bayes classifiers.
Additionally, ML can assist in the automatic generation of signatures for known threats or applications. By analyzing historical data and patterns, ML models can create signatures that can be used to detect similar traffic in the future.
SSL/TLS Interception
A Solution for HTTPS Encryption Some firewalls now offer HTTPS inspections (Firewall SSL/TLS Interception), which would decrypt the HTTPS-protected traffic and determine whether the content can pass through.
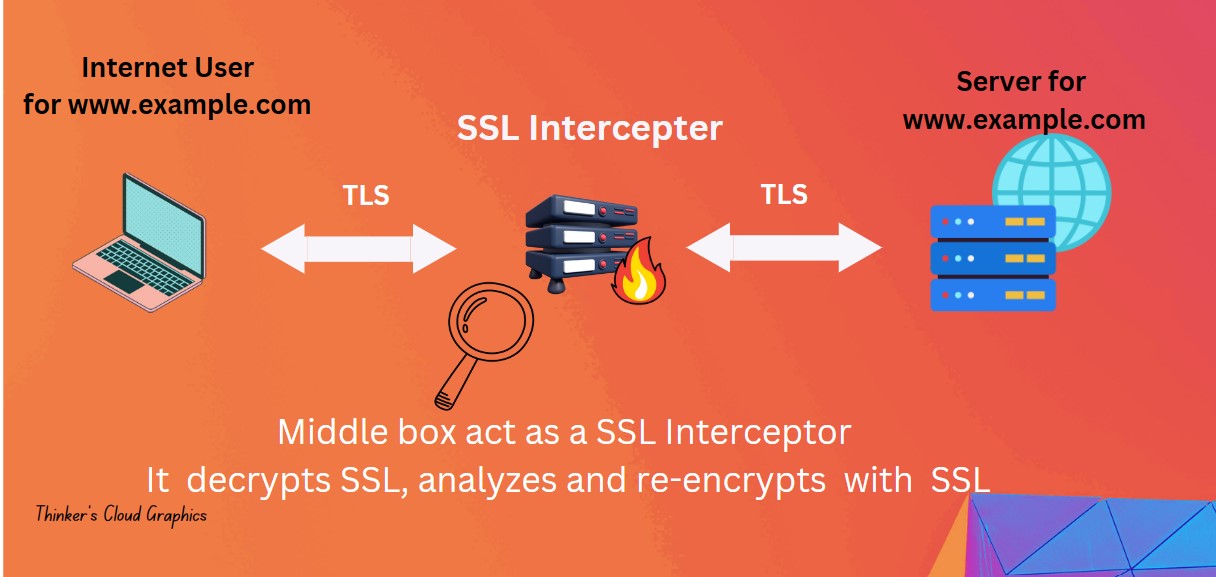
According to the above illustration,
- The middle box (a firewall) decrypts the incomming packets from the Server or the client using its own a dynamic SSL certificate.
- Then read the decrypted payload using above DPI methods and extract usefull information for application and threat detection.
- Finally, it re-encrypt the packet using a certificate and forward to the receiving end.
Users’ browsers must trust this certificate, which is usually signed by a local certificate authority (CA) configured on the security device.
Applications of DPI
Application Identification
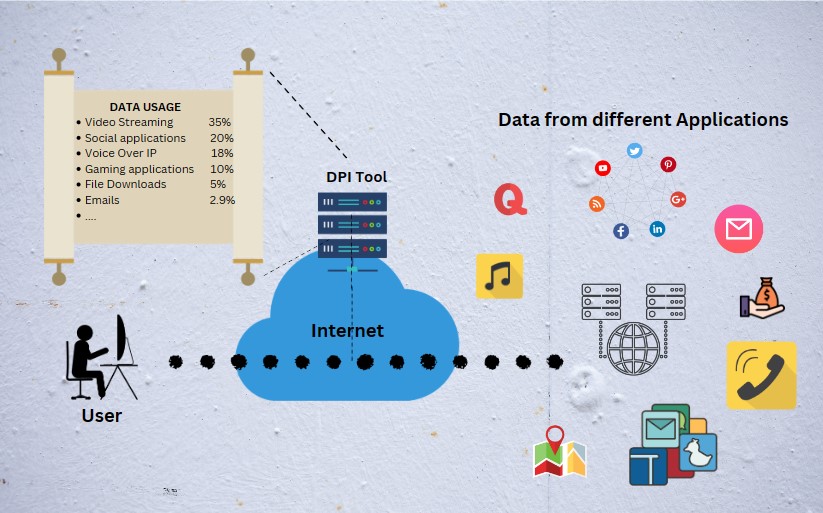
DPI classifies and identifies applications running on a network, offering insights into application-level traffic patterns and enabling policy enforcement. This is most common because application wise traffic and usage monitoring is an essential need of any ISP. (Ex: ISPs offer data packages with high priority for business critical applications )
Network Security
Quality of Service (QoS)
DPI is crucial for managing network traffic, ensuring optimal performance for critical applications by prioritizing and allocating bandwidth based on application needs.
